Com.bot Enterprise Role-Based Access Control
In today’s digital landscape, secure collaboration and effective access management are important for businesses managing difficult team environments. Com.bot Enterprise meets the challenge with its strong Role-Based Access Control (RBAC), ensuring that the right people have the right access at all times.
This article explores how RBAC functions within Com.bot Enterprise, alongside key features like Single Sign-On (SSO), team roles, permission scopes, and audit logs.
Learn how these tools help organizations to support secure and efficient teamwork.
Key Takeaways:
- Com.bot Enterprise offers secure multi-team collaboration through SSO, granular team roles, permission scopes, and audit logs.
- RBAC in Com.bot Enterprise allows for efficient management of team access and permissions.
- Using SSO with Com.bot Enterprise makes it safer and easier for team members to log in.
- 1 What is Com.bot Enterprise?
- 2 What is Role-Based Access Control (RBAC)?
- 3 What is Single Sign-On (SSO)?
- 4 What are Team Roles?
- 5 What are Permission Scopes?
- 6 What are Audit Logs?
- 7 Frequently Asked Questions
- 7.1 1. What is Com.bot Enterprise Role-Based Access Control?
- 7.2 2. How does Com.bot Enterprise support SSO?
- 7.3 3. Can Com.bot Enterprise Role-Based Access Control be customized for different teams?
- 7.4 4. What are permission scopes in Com.bot Enterprise Role-Based Access Control?
- 7.5 5. Is there a way to track user activity and changes within Com.bot Enterprise?
- 7.6 6. How does Com.bot Enterprise Role-Based Access Control provide safe teamwork between several groups?
What is Com.bot Enterprise?
Com.bot Enterprise is a platform that supports secure collaboration between multiple teams. It includes features such as Single Sign-On (SSO), role-based access control (RBAC), and detailed audit logging.
These tools help organizations manage permissions and sensitive information, keeping security roles the same and making access management easier. With strong user management and adherence to industry standards, Com.bot Enterprise allows businesses to organize workflows without risking data integrity or security. To further enhance operational efficiency, consider how tools like Com.bot’s Appointment Booking Bot can streamline scheduling tasks within secure environments.
What is Role-Based Access Control (RBAC)?
Role-Based Access Control (RBAC) is a security method that limits system access to users with specific permissions based on their roles, which match their job duties in a company.
This method allows managers to establish security roles and user permissions, ensuring workers only access the information and tools required for their tasks.
By using RBAC, companies can improve security by following the rule of least privilege, which reduces the chance of unauthorized access and privilege misuse.
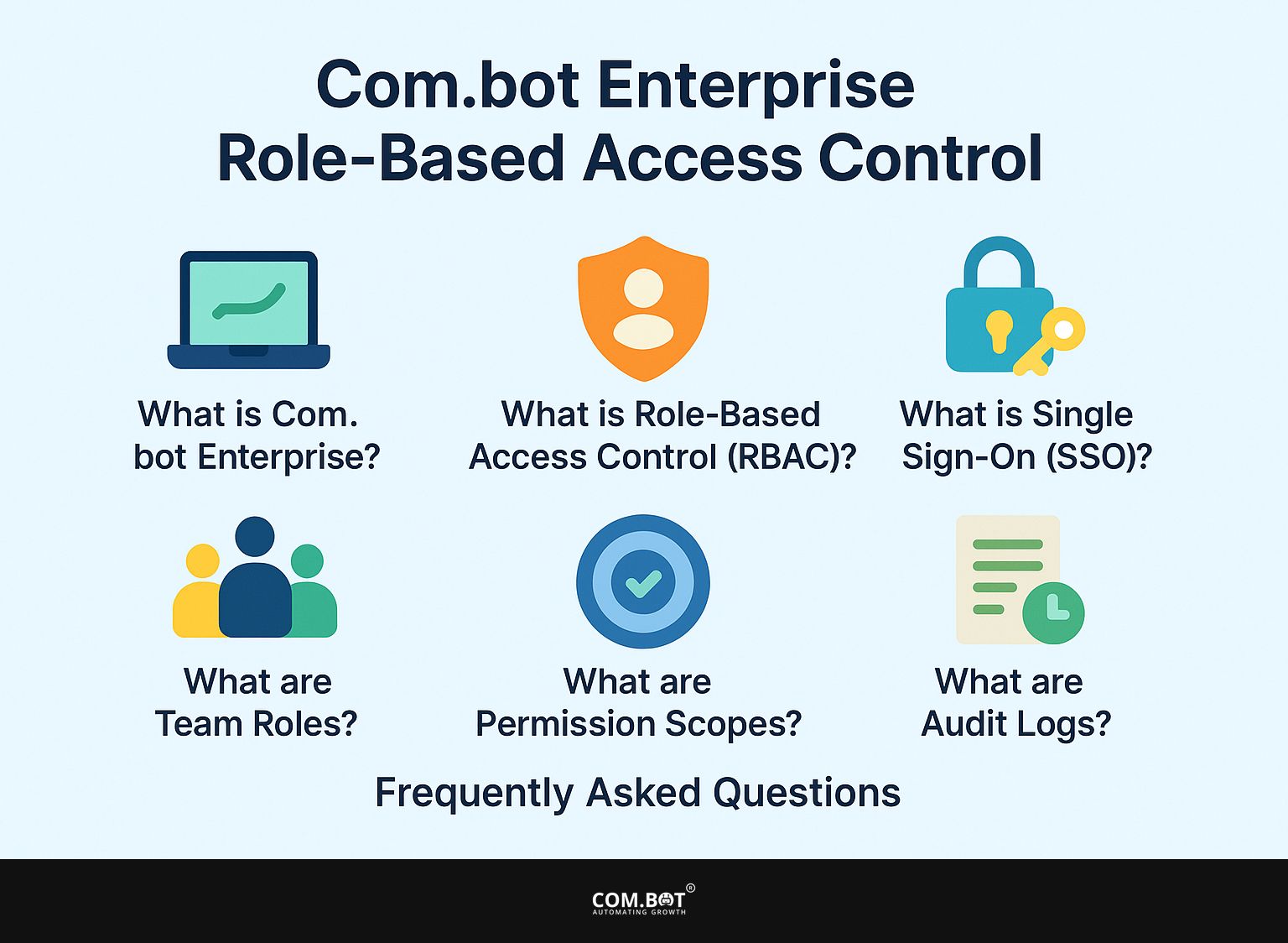
How does RBAC work in Com.bot Enterprise?
In Com.bot Enterprise, RBAC is integrated into the user management system, allowing administrators to create and assign roles that determine user permissions across various channels and workflows. This enables a clear structure for managing user roles, ensuring that each employee has the specific access required for their job while maintaining security practices that protect sensitive data from unauthorized access. The system works with hierarchical and restricted RBAC models, improving the detail of access control.
- For example, roles like ‘Administrator,’ ‘Manager,’ and ‘Employee’ can be clearly outlined, with each role having specific permissions suited to their tasks.
- An administrator can easily set roles through the user interface, based on user information or business needs.
- If a user’s responsibilities change, roles can be modified seamlessly, ensuring they receive the appropriate permissions without compromising security.
- This clear process allows higher-level roles to automatically receive permissions from lower-level roles, simplifying security rule management and decreasing the effort needed to oversee them.
What is Single Sign-On (SSO)?
Single Sign-On (SSO) is a way to log in that allows users to access various apps and services using just one username and password, simplifying the process and increasing security.
By using an authentication provider, SSO removes the need to log in multiple times, lowering the chance of password overload and security issues. This simpler way of handling access is especially helpful in businesses, where keeping track of user identity across different platforms is important for keeping security roles and following rules.
1. How does Com.bot Enterprise support SSO?
Com.bot Enterprise supports Single Sign-On (SSO) through seamless integration with leading authentication providers, allowing users to log in once and gain access to all connected applications effortlessly. This support for SSO improves role-based access control by ensuring user identities are verified consistently across different services, simplifying access management and enhancing security.
By reducing the number of credentials users need to remember, Com.bot Enterprise minimizes potential security risks associated with password management. Plus popular providers like Google, Microsoft, and Okta, Com.bot Enterprise also accommodates a range of custom authentication solutions to cater to diverse organizational needs.
The variety of supported providers simplifies the process for users and makes it easier to start using new applications. By creating specific RBAC, organizations can clearly outline user roles and permissions, increasing security by ensuring individuals only access the information necessary for their tasks.
Companies gain from a unified access management plan that improves security and increases productivity by allowing users to move through their digital space smoothly.
2. What are the benefits of using SSO with Com.bot Enterprise?
Using Single Sign-On (SSO) with Com.bot Enterprise offers many advantages, such as better user experience, stronger security, and simpler compliance with industry regulations. By enabling users to access multiple services with one login, SSO reduces the friction associated with managing multiple credentials while simultaneously reinforcing security roles through centralized access control.
This centralized method improves access management and follows IAM system guidelines to help organizations stay compliant and safeguard important data.
The simplified process increases productivity and reduces the chance of password problems, protecting company resources. When people use different apps easily, they enjoy a better user experience, which results in greater satisfaction and less time needed to get started. SSO assists with following regulatory rules, simplifying reporting and audits.
This means that organizations can more easily demonstrate adherence to critical standards, all while improving their overall security posture. Com.bot Enterprise users get an easy-to-use system that combines convenience, safety, and compliance smoothly.
What are Team Roles?
Team roles in Com.bot Enterprise define the tasks and permissions given to users in a group setting. By setting clear user roles and matching security roles, organizations can make sure team members have the right access needed to do their work well.
This way of assigning roles helps in managing projects effectively and improves security by clearly setting access limits based on team roles.
1. What are the different team roles in Com.bot Enterprise?
In Com.bot Enterprise, the different team roles include administrators, project leads, quality engineers, and various user roles that correspond to specific permissions and responsibilities. Each role is designed to facilitate effective collaboration while ensuring that security roles are appropriately assigned to prevent unauthorized access to sensitive information.
This organized method helps organizations manage projects well and keep clear accountability. Administrators hold overarching control, with the ability to manage user permissions and system settings, thus ensuring a secure environment.
Project leads, tasked with overseeing project execution, coordinate team efforts and resource allocation while ensuring that tasks are completed on time.
Quality engineers make sure products function properly and are reliable by performing detailed tests, which is a key part of developing products.
Different user roles are set up for particular jobs, granting restricted access based on their duties, which improves teamwork and safety in the process. Clearly defining roles encourages responsibility and improves efficiency in teams.
2. How are team roles assigned in Com.bot Enterprise?
Team roles in Com.bot Enterprise are given out by administrators who look at job duties and match them with the right permissions and security roles. This process of assigning roles gives each user the right level of access needed to do their job well and reduces the chance of unauthorized access.
By using a clear order and organized user management, organizations can keep control over resource access and improve teamwork.
In this system, managers carefully examine the tasks associated with each job, considering factors such as team cooperation, project requirements, and individual skills. They use certain tools to check existing roles without manual effort, helping to match user permissions with standard security guidelines.
This careful method improves security in organizations by stopping unauthorized entry and encourages responsibility, as employees know their access boundaries.
This approach improves productivity by giving users necessary permissions and protecting sensitive information through a strong role definition plan.
What are Permission Scopes?
Permission scopes set the limits on what users can access within Com.bot Enterprise, matching access to the specific jobs of each user.
By clearly defining these scopes, organizations can make sure that permissions fit the security roles given to each user. This helps protect important information and supports smooth workflow management.
This clear method of handling access is essential for following rules and helping team cooperation.
1. How do permission scopes work in Com.bot Enterprise?
In Com.bot Enterprise, permission scopes work by allowing administrators to specify detailed access levels for different user roles across various features and resources. This granular control enables organizations to align permissions with the specific security roles assigned to each user, ensuring that sensitive information is only accessible to authorized personnel.
By clearly setting these boundaries, Com.bot Enterprise helps in assigning roles correctly and improves access management. For instance, a project manager may possess permissions to edit and delete documents, while team members may only have view access.
This structure protects important data and makes work processes smoother by giving users the exact tools they need for their jobs, avoiding extra permissions that are not needed.
Through the implementation of fine-grained access control, organizations can confidently comply with industry regulations and internal policies, thereby mitigating risks associated with data breaches or unauthorized access. Com.bot Enterprise allows organizations to set up a secure area that suits their work requirements.
2. What are the different permission scopes available in Com.bot Enterprise?
Com.bot Enterprise offers various permission scopes that cater to the diverse needs of teams and users, ensuring that access management aligns with organizational security policies. These scopes include read, write, delete, and custom permissions, allowing flexibility in how resources are accessed and modified based on user roles and responsibilities.
By implementing these distinct permission scopes, organizations can effectively safeguard sensitive data and maintain control over resource management. The option to set different access levels allows each team to work according to their own needs while still following the overall security rules.
For instance, an administrator might be granted full control, including the capacity to modify permissions for others, while a team member might only need read access to certain documents or tools. This division makes sure that important tasks are only done by authorized staff, reducing the chance of changes or data breaches by unauthorized people.
The customized access management offered by Com.bot Enterprise increases work efficiency and strengthens the security of company data.
What are Audit Logs?
Audit logs in Com.bot Enterprise are detailed records that show user activities, permission changes, and access events, ensuring clarity and safety for teamwork across different groups.
By keeping detailed records of what happens in the system, organizations can verify compliance with security rules and standards, ensuring user roles align with assigned permissions.
This feature improves accountability and helps find possible security issues or unauthorized access to important information.

1. How do audit logs help with secure multi-team collaboration in Com.bot Enterprise?
Audit logs in Com.bot Enterprise make collaboration among multiple teams more secure by keeping a record of user actions, changes to permissions, and access activities, ensuring a clear record for accountability. This level of monitoring is important for following company rules and legal requirements, as it allows teams to check user actions and make sure security rules are being followed.
By using detailed audit records, organizations can create a culture of openness and confidence among team members. The detailed information in these logs is an important tool for spotting possible security problems or policy breaches, allowing teams to quickly address any unusual activities.
They play an essential role in evaluating the effectiveness of access controls and permissions, ensuring that only authorized individuals have the ability to access sensitive information.
Audit logs help with internal checks and offer required documentation for outside compliance reviews, showing their role in keeping organizations honest and users responsible in group settings.
2. What information is included in audit logs in Com.bot Enterprise?
Audit logs in Com.bot Enterprise include detailed information about user activities, such as login attempts, changes to permissions, resource access events, and modifications made to user roles. This data helps organizations track compliance with security rules and manage access effectively.
By examining these logs, teams can find trends, spot unusual activities, and confirm that security measures are followed across the organization.
The logs capture timestamps, IP addresses, and the specific actions taken by users, enabling teams to track who accessed what information and when. This information is important for identifying unauthorized access attempts and confirming that users have the correct permissions for their roles.
Checking changes in user permissions is important for keeping a secure environment. It helps organizations make sure that users have the minimum access they need and change access rights when job roles or performance change. Audit logs are helpful for security, checking compliance, looking into internal problems, and examining operations.
Frequently Asked Questions
1. What is Com.bot Enterprise Role-Based Access Control?
Com.bot Enterprise Role-Based Access Control is a security feature that allows for granular control over user permissions and access within the Com.bot Enterprise platform.
2. How does Com.bot Enterprise support SSO?
Com.bot Enterprise lets users sign in using their current login details securely. It works with well-known systems like SAML and OAuth for Single Sign-On (SSO).
3. Can Com.bot Enterprise Role-Based Access Control be customized for different teams?
Yes, Com.bot Enterprise provides granular team roles that can be customized to fit the specific needs of different teams within an organization.
4. What are permission scopes in Com.bot Enterprise Role-Based Access Control?
Permission scopes refer to the specific actions or functions that a user is allowed to perform within the Com.bot Enterprise platform. These can be set at the channel or flow level for better control.
5. Is there a way to track user activity and changes within Com.bot Enterprise?
Yes, Com.bot Enterprise has built-in audit logs that allow for easy tracking and monitoring of user activity within the platform, providing an added layer of security and accountability.
6. How does Com.bot Enterprise Role-Based Access Control provide safe teamwork between several groups?
Com.bot Enterprise provides a secure environment for teams to collaborate by allowing for customizable roles, permission scopes, and audit logs, ensuring that sensitive information is only accessible to authorized individuals.